I've been scratching my head on this problem over the past two hours and I'm evidently missing something about the subject matter.
For the past two weeks I've been accessing my NAS remotely and deployed a number of docker containers delivering services like Nextcloud, a Jekyll blog, etc.
I've purchased a domain, generated Letsencrypt certificates and configured a reverse-proxy (Traefik) to forward all incoming requests to the appropriate service
Everything was and is working perfectly from the Internet or VPN: the Nextcloud client could connect to the server without issues, the browser was correctly handling https and showing my websites as secure, etc.
But today I'm back home and connected to my LAN and I'm getting all sorts of certificate errors while accessing the same services locally.
I'm trying to zero in into the possible culprit and I guess it's either the reverse-proxy server or the NAS itself.
I tend to think it's the latter because Traefik is not generating any log file when I'm trying to access the services from the LAN as if the requests are being trapped somewhere before they hit the reverse-proxy.
Take Nextcloud for example: when I try to open the site using the browser (I'm getting a similar error when launching the Netcloud client) at (say) https://nextcloud.mydomain.com the browser shows a MOZILLA_PKIX_ERROR_SELF_SIGNED_CERT error. If I display the certificates that the browser sees I get QNAP's instead of my own!
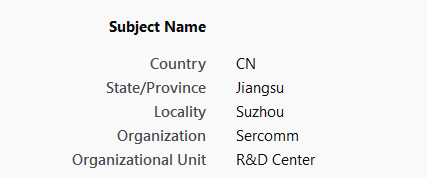
Why the heck is my letsencrypt certificate not being delivered and QNAP's instead is??
Why is that error displayed if:
1) The browser (even in the LAN) is (or should be) still trying to reach the server via the FQDN domain name which resolves into my router's public IP
2) and then hit Traefik which forwards the request to the appropriate container using the domain SSL certificates
3) which finally responds to the original client (the browser)
It seems like the clients requests when running in the LAN are not handled via the 1-2-3 chain above and the correct SSL certificates are not correctly delivered.
Like I said: everything works perfectly when I am connecting from the internet and not from the LAN.
I'm completely clueless and I'd appreciate some help.
Thanks
Regards